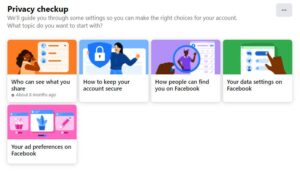
After the recent supreme court ruling overturning Roe vs Wade, many of you are rightfully concerned about your rights, your health, and your safety. One of the ways this has manifested is mistrust of many period tracker apps when you can’t control your data or ensure it’s being properly safeguarded- the worry being that the data will be given or sold to states that are adding criminal penalties for abortions, other losses of pregnancy, and other forms of heath care. Many users have started uninstalling their period tracker apps out of concern, particularly those in such states.
Today, Operation Safe Escape began development of a period tracker app that we will make available for free for Android and iOS. There will be no ads or monetization of any kind. Additionally, the following privacy features are intended to keep users safe and able to make health decisions without compromising their safety or sense of safety:
- The app will not access the internet for any reason
- The only data collected by the app will be what the user enters and what is necessary for the app to function on the device. None of this data will ever be sold, shared, or given away. Since even we can’t access it, we couldn’t anyway
- The information will exist only on the user’s device, not the cloud
- All data will be encrypted
- All data on the app will be in control of the user, and the app will allow a quick wipe of the data
- There will be a space for safety resources and links
Critically, the app will be open source to allow the community (and the users themselves) to know exactly what the app is doing and how their data is being stored. There should be nothing to hide. We will be looking for other ways to protect users from other threats, such as cases where an abusive partner may get access to the device.
More information will be provided as development continues. If you have any input or ideas, please feel free to reach out at [email protected]
Reproduction and body autonomy is a common target by abusers. Reproductive coercion is a form of abuse where the abuser forces the victim to get pregnant or terminate a pregnancy against their will. According to the National Coalition Against Domestic Violence, 25% of domestic violence survivors have experienced this form of abuse. Reproductive health is directly related to domestic violence, and Operation Safe Escape stands against all forms of abuse.
June 28, 2022 update:
The question was asked, why create a new tool versus supporting existing open source projects? That’s a great question.
Historically, we’ve tried both creating our own tools and requesting changes / updates to existing open source ones. We admire and appreciate the open-source maintainers; they keep the world running. But we have to consider and include our primary mission in everything that we do. I this case, ensuring that the users impacted by domestic violence and stalking have their concerns and needs quickly addressed. This is something we want to do to help everyone, but survivors of abuse sometimes have different needs. Our perception of risk doesn’t stop with any government, although this is certainly a concern. We’re not only concerned about government overreach and weaponization of the courts, we’re also concerned about the abuser trying to control the individual’s fundamental reproductive rights. By developing our own tool, change control and approval is less of a concern. For example, including information and resources on reproductive coercion might seem important to us, but might not be a change that’s accepted on another team’s app (not assuming, just an example). Another issue is that abusers adapt quicker than the government does, so the ability to very quickly add new features, information, and tools can make a major difference for a specific set of users.

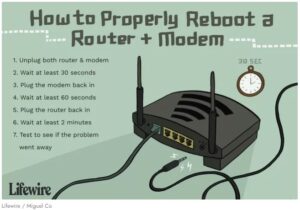
 login screen. The username and password, if it hasn’t been changed, will be found in the documentation provided with the router. If it’s been changed or if you don’t know that information, contact your ISP and they’ll help you recover the information. You might also find the default login information online by searching “default login” and your router model number.
login screen. The username and password, if it hasn’t been changed, will be found in the documentation provided with the router. If it’s been changed or if you don’t know that information, contact your ISP and they’ll help you recover the information. You might also find the default login information online by searching “default login” and your router model number.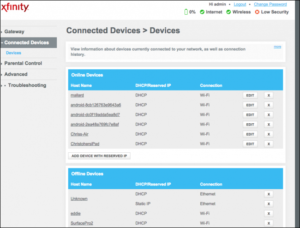
 A court-ordered name change is obtained by petitioning the court in the county in which you reside. This is generally approved, unless the court believes that the name change is intended to defraud creditors. If everything is in order the court will issue an order authorizing you to start using the requested name.
A court-ordered name change is obtained by petitioning the court in the county in which you reside. This is generally approved, unless the court believes that the name change is intended to defraud creditors. If everything is in order the court will issue an order authorizing you to start using the requested name. 
 Until relatively recently, the Social Security Administration (SSA) would not issue a new number unless there was evidence that the number itself had been misused. Fortunately, this is no longer necessary in cases of harassment or abuse.
Until relatively recently, the Social Security Administration (SSA) would not issue a new number unless there was evidence that the number itself had been misused. Fortunately, this is no longer necessary in cases of harassment or abuse.  “I know people always ask me why I run sexual assault, domestic violence and human trafficking legislation, and I think I do it because someone has to be that voice,” Romero said. “And in the time of COVID right now, there are a lot of people in very vulnerable situations. I want to make sure that we continue to say, ‘We see you’ and they get the help they need and they protect themselves, their children and their pets.”
“I know people always ask me why I run sexual assault, domestic violence and human trafficking legislation, and I think I do it because someone has to be that voice,” Romero said. “And in the time of COVID right now, there are a lot of people in very vulnerable situations. I want to make sure that we continue to say, ‘We see you’ and they get the help they need and they protect themselves, their children and their pets.”